Pwn2Own Automotive 2025 - Day Three and Final Results
January 23, 2025 | Dustin ChildsWelcome to the third and final day of Pwn2Own Automotive 2025. Over the past two days, we have awarded $718,250 for 39 unique 0-days. Sina Kheirkhah has a commanding lead for Master of Pwn, but anything can happen. Here’s a look at today’s results…
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a single bug to exploit the ChargePoint EV charger. He earns himself another $25,000 and 5 Master of Pwn points.
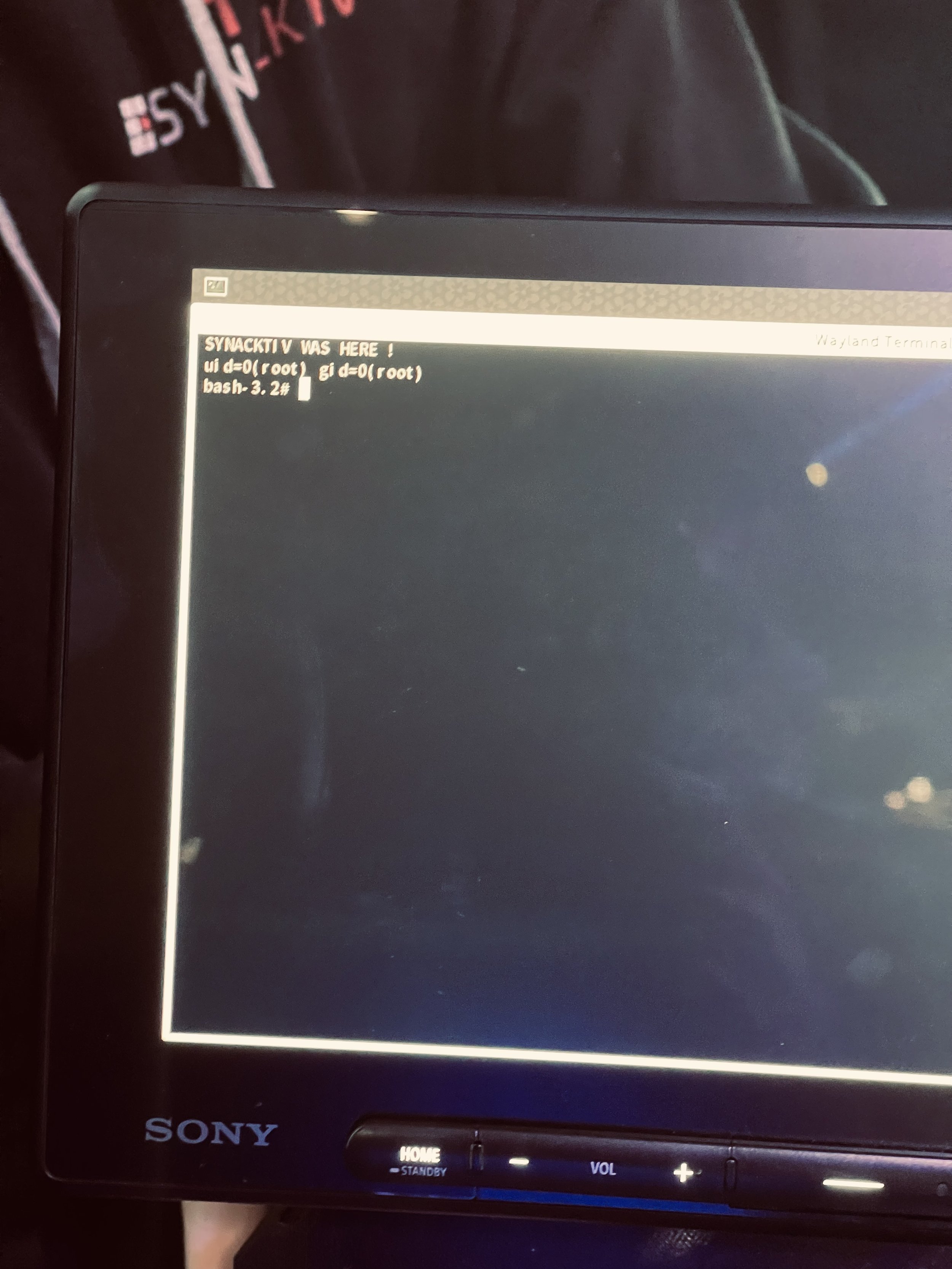
SUCCESS - The Synacktiv (@Synacktiv) team used a single integer overflow to exploit the Sony IVI. Their work earns them another $10,000 and 2 Master of Pwn points.
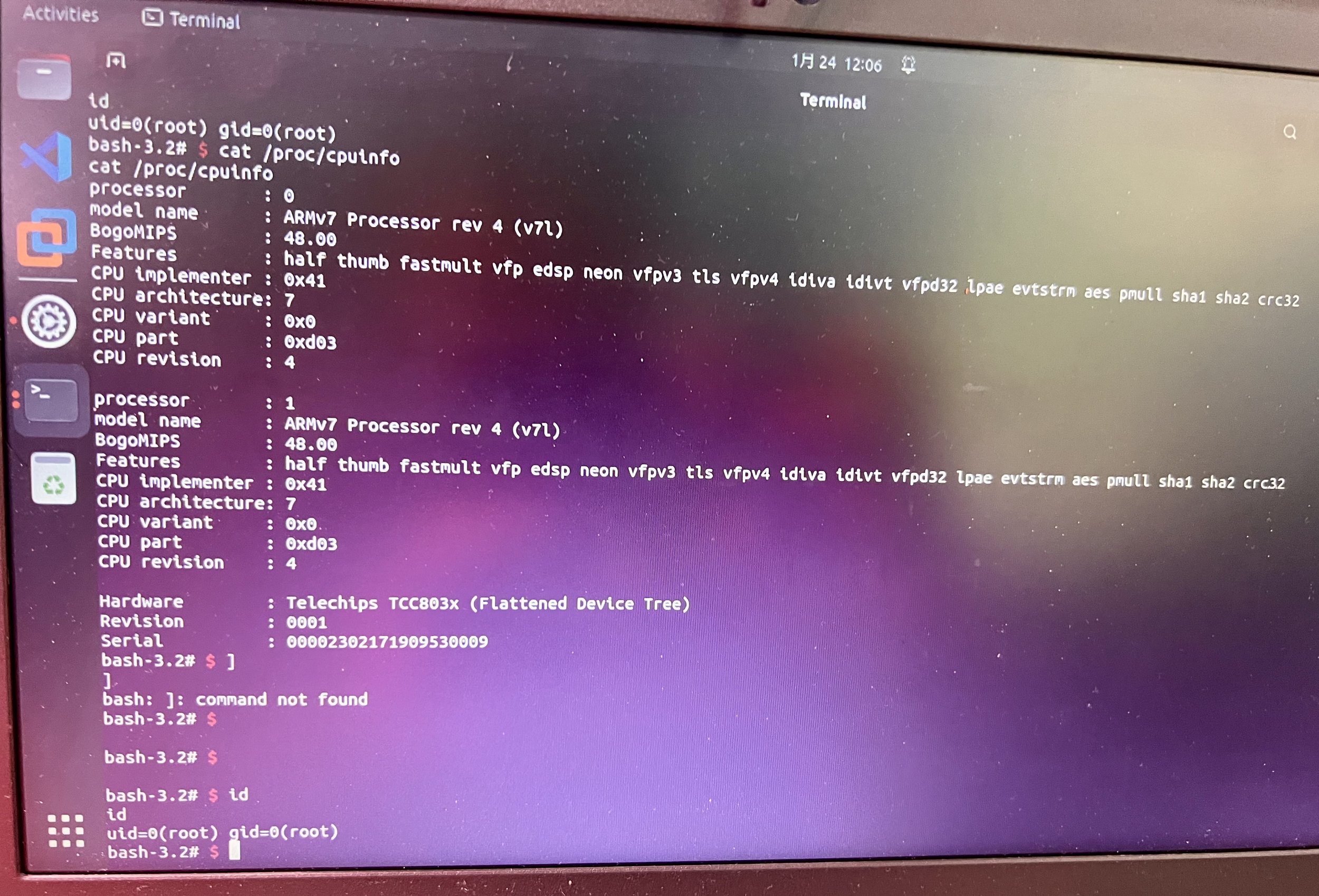
SUCCESS - The Synacktiv (@Synacktiv) team used a single buffer overflow to exploit the Autel MaxiCharger. They were also able to demonstrate signals being transmitted via the Charging Connector for the add on. This work earns them $35,000 and 6 Master of Pwn points.
SUCCESS/COLLISION - Bongeun Koo (@kiddo_pwn) of STEALIEN used three bugs to exploit the Ubiquiti charger, but two were already known. He still wins $26,750 and 4.5 Master of Pwn points.
SUCCESS - Thanh Do (@nyanctl) of Team Confused was able to confuse the Alpine iLX-507 with a single stack buffer overflow. The unique bug earns him $10,000 and 2 Master of Pwn points.
SUCCESS - The PHP Hooligans again show their expertise by using a single OS command injection bug to exploit the Kenwood DMX958XR. Their final attempt of the contest earns them another $10,000 and 2 Master of Pwn points.
SUCCESS/COLLISION - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of fuzzware.io used a two bug chain - including an uninitialized variable - to exploit the WOLFBOX EV charger. However, one of these bugs was previously known. The earn $18,750 and 2 Master of Pwn points.
COLLISION - Rob Blakely and Andres Campuzano of the Technical Debt Collectors successfully exploited the Tesla Wall Connector, but they used a previously known bug. They still earn $12,500 and 2.5 Master of Pwn points.
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a command injection bug for his last exploit of the contest. He was able to pop the Alpine iLX-507 and earn himself another $10,000 and 2 more Master of Pwn points.
SUCCESS - The final attempt of the contest was the Pwn2Own debut of Evan Grant (@stargravy). He successfuly used an OS command injection bug to exploit the Kenwood DMX958XR. His unique approach earns him $10,000 and 2 Master of Pwn points.
And that’s a wrap! Pwn2Own Automotive 2025 is complete. In total, we awarded $886,250 for 49 0-days over the three day competition. With 30.5 points and $222,250 awarded, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) is our Master of Pwn. Here’s the top five standings:
Thanks to all of the researchers and vendors who attended. Without their hard work and dedication, none of this would be possible. Thanks also to our partners at VicOne and our sponsor Tesla. Their partnership has been invaluable. Stay tuned for upcoming announcements about future Pwn2Own competitions. We have a lot in store. See you then!