Pwn2Own Ireland 2024: Day Two Results
October 23, 2024 | Dustin ChildsWelcome back to Pwn2Own Ireland 2024! Yesterday, we awarded $516,250 for over 50 unique 0-day bugs. Today looks to be just as exciting with attempts on phones, cameras, printers, and smart speakers. We’ll be updating this blog in real time as results become available. We have a full schedule of attempts today, so stay tuned! All times are Irish Standard Time (GMT +1:00).
That's a wrap on Day 2 of Pwn2Own Ireland! Today, we awarded $358,625 - which brings the event total to $874,875. The Viettel Cyber Security team has a commanding lead for Master of Pwn, but with two days left, there still could be changes.
SUCCESS - Pham Tuan Son (@Little_timmy) and ExLuck (@ExLuck99) from ANHTUD used a single stack-based overflow to exploit the Canon imageCLASS MF656Cdw printer. Their second-round win earns them $10,000 and 2 Master of Pwn points.
SUCCESS - Ken Gannon (@yogehi) of NCC Group (@NCCGroupInfosec) used five different bugs, including a path traversal, to get a shell and install an app on the Samsung Galaxy S24. He earns $50,000 and 5 Master of Pwn points.
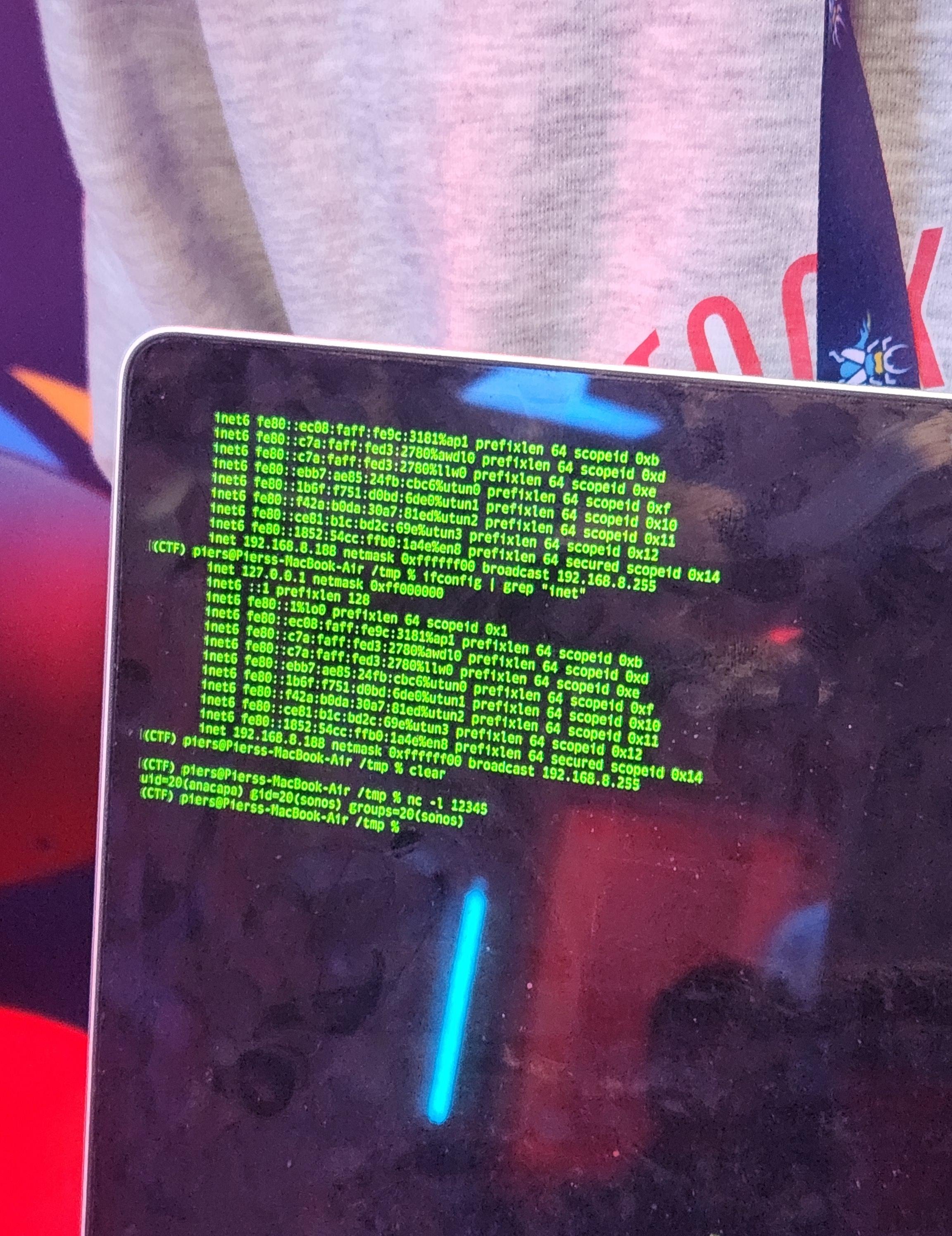
SUCCESS - dungdm (@_piers2) with Viettel Cyber Security (@vcslab) used a single Use-After-Free (UAF) bug to exploit the #Sonos Era 300. The second-round win earns him $30,000 and 6 Master of Pwn points.
COLLISION - The Tenable Group used a stack-based buffer overflow to exploit the Lorex 2K camera, but the bug had already been used in the contest. They still earn $3,750 and 1.5 Master of Pwn points.
SUCCESS - Viettel Cyber Security (@vcslab) used a single type confusion bug to exploit the HP Color LaserJet Pro MFP 3301fdw. The second-round win earns them $10,000 and two Master of Pwn points.
FAILURE - The DEVCORE Research Team (@d3vc0r3) and nella17 (@nella17tw) working with DEVCORE Internship Program couldn't get their SOHO Smashup completed in time. They made it through the router but couldn't pop the printer.
FAILURE - Ryan Emmons (@the_emmons) and Stephen Fewer (@stephenfewer) of Rapid7 could not get their exploit og the Lorex 2K camera working within the time allotted.
SUCCESS - The InfoSect (@infosectcbr) group used a heap-based buffer overflow to take over the Sonos Era 300 speaker. Their second-round win earns them $30,000 and six Master of Pwn points.
SUCCESS - Chris Anastasio (@mufinnnnnnn) and Fabius Watson (@FabiusArtrel) of Team Cluck used two bugs (including a CLRF injection) in a beautiful chain to exploit the QNAP TS-464 NAS. The second round win earns them $20,000 and 4 Master of Pwn points.
FAILURE - Cody Gallagher and Charlie Waters could not get their exploit of the Sonos Era 300 working within the time allotted.
SUCCESS - PHP Hooligans / Midnight Blue (@midnightbluelab) used a command injection bug to get code execution on the Synology BeeStation BST150-4T. They earn $40,000 and four Master of Pwn points.
COLLISION - Corentin BAYET (@OnlyTheDuck) of @Reverse_Tactics used three bugs to go from the QNAP QHora-322 to the QNAP TS-464, but 1 had been previously seen in the contest. He still earns $41,750 and 8.5 Master of Pwn points.
FAILURE - Unfortunately, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) could not get his exploit of the TrueNAS Mini X working within the time allotted.
FAILURE - Sadly, the Neodyme (@Neodyme) team could not get their exploit of the Lexmark CX331adwe printer working within the time allotted.
SUCCESS - Chris Anastasio (@mufinnnnnnn) & Fabius Watson (@FabiusArtrel) of Team Cluck used an Improper Certificate Validation bug to exploit the Synology DiskStation. Their second round win earns them $20,000 and four Master of Pwn points.
COLLISION - The Synacktiv (@Synacktiv) team successfully exploited the Synology Beestation, but they used a bug previously seen during the contest. They still earn $10,000 and 2 Master of Pwn points.
COLLISION - Compass Security (@compasssecurity) ran into a collision in their attempt against the Ubiquiti AI bullet. Their exploit still wins them $3,750 and 1.5 Master of Pwn points.
SUCCESS - YingMuo (@YingMuo) working with DEVCORE Internship Program used an argument injection and a SQL injection to get their root shell on the QNAP TS-464 NAS. Their third-round victory gets them $20,000 and 4 Master of Pwn points.
SUCCESS / COLLISION - Our final SOHO Smashup of Day 2 ends with a partial collision. Neodyme (@Neodyme) used four bugs, including a stack-based buffer overflow, in their successful demonstration, but one bug had previously been used in the contest. They earn $21,875 and 8.75 Master of Pwn points.
COLLISION - One of our final attempts of Day 2 ends in a collision. The InfoSect (@infosectcbr) group successfully got a shell on the Lorex camera, but they used a bug previously seen in the contest. They still earn $3,750 and 1.5 Master of Pwn points.
success - Our final exploit of the day had NiNi (@terrynini38514) of DEVCORE Research Team exploit the AeoTec Smart Home Hub with an Improper Verification of Cryptographic Signature bug. They earn $40,000 and 4 Master of Pwn points.